Accountability, APIs, and the United States of Surveillance
What does a license plate scan, a REST API, and a knock on someone’s door have in common? In Minneapolis, they’ve become one in the same. Net API Notes for 2026/02/03, Issue 257.

What a start to 2026. Time didn't just speed up; it skipped steps, ignored the laws of gravity, and is now flying.
How is everybody doing? Did you kick off the year with a few new resolutions? Learn a new joke? Reorganize your home office? Wake up one morning to discover 3,000 federal agents - outnumbering our local police forces- roaming your city's streets, abducting people without cause, and daring onlookers to test whether the Constitution still applies?
Yeah. It's been that kind of January in Minneapolis and St. Paul - the Twin Cities my family and I have called home since 2021.
And as strange as it may sound, the story of Operation Metro Surge* - the scale of it, the coordination of it, the quiet efficiency with which it evolves - is, in no small part, a story about APIs.
I am so incredibly proud of the way the communities throughout Minnesota have rallied to support one another. This is a culture that has had its "neighborliness" tested and rallied in a way that would make Mr. Rogers proud. Ordinary people are loading cars with food and toiletries to deliver to terrorized families in hiding. These are folks standing vigilant in freezing weather to protect kids' schools from opportunistic cullings. Then there are the whistle-wielding drivers patrolling for masked agents. (For more on what everyday life is like during this past month, I highly recommend this detailed and articulate recap by Minnesota State Senator Erin May Quade.)
But as these leaderless convoys successfully swarmed ICE agents, tactics changed. The agents stopped scurrying away and started scanning.
The Architecture of Intimidation
As documented in numerous places in as many weeks, federal agents are increasingly scanning the license plates of observer vehicles. Sometimes, nothing happens. Other times, those federal agents show up at observers' homes, using people's full names and issuing "final warnings", a clear intimidation tactic. In another case, an agent is recorded scanning a vehicle plate. When asked what they're doing, they tell the observer they're "now you're considered a domestic terrorist" and "good luck with that". I might dismiss it as juvenile bluster, except a Minnesota executive had her Global Entry and TSA PreCheck privileges revoked only three days after an incident in which she observed activity by immigration agents. All for the crime of holding a camera and attempting some oversight where there was none. (More reporting on the purpose and use of these watchlists is available from Ken Klippenstein.)
The part that federal agents interact with is a mobile app. Journalists Joseph Cox (404 Media, links 1 and 2) and Amanda Chavez (Mijente) have extensively documented the "Mobile Companion" app used by ICE agents. (A separate app, "Mobile Fortify", is used for facial recognition.)
The License Plate Recognition (LPR) scanner was developed by Motorola Solutions (specifically their Vigilant Solutions subsidiary). Once the app has license plate information, it is then passed to CLEAR, a Thomson Reuters data broker product.
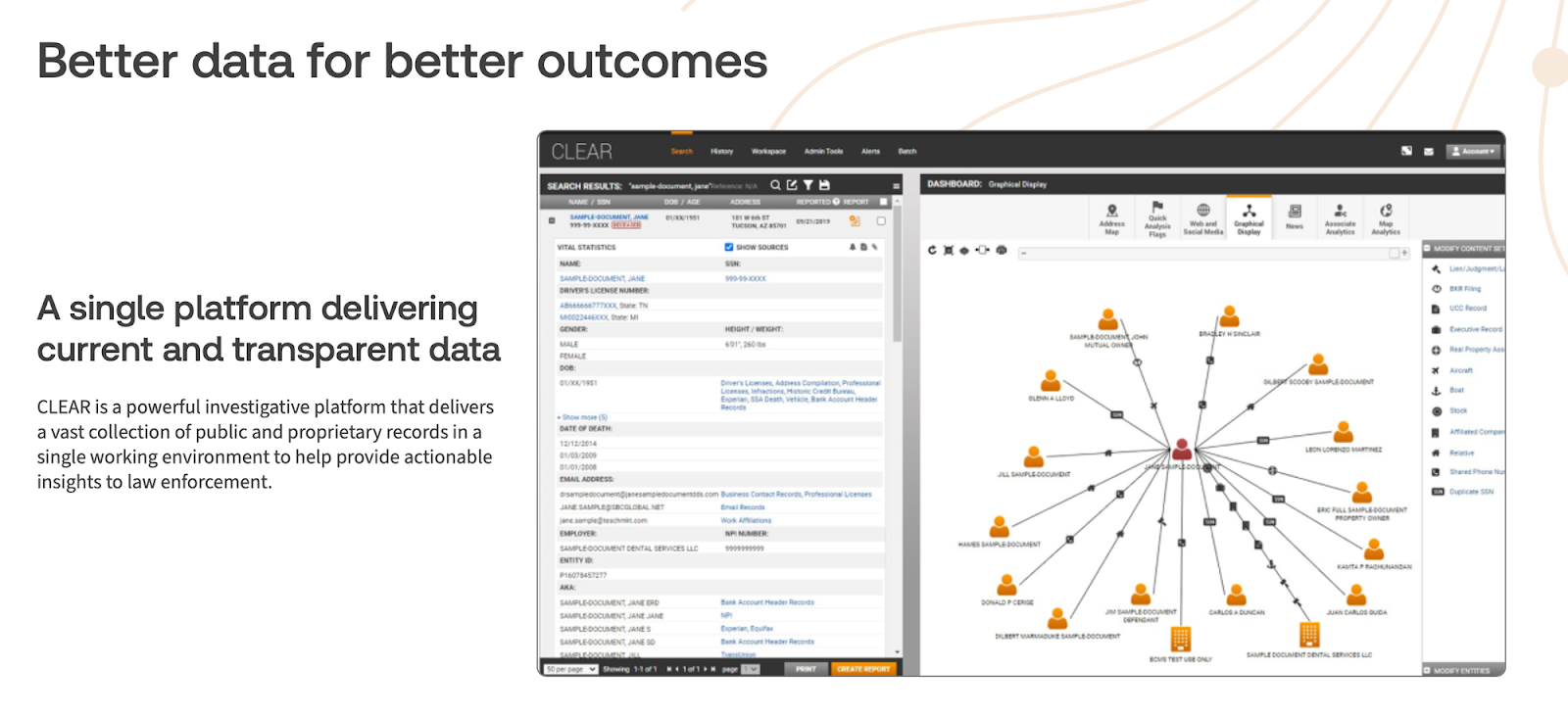
An agent scans a plate in the field; the app then makes an immediate API call to the CLEAR database. Thomson Reuters doesn't make developer documentation outside of select patterns (for good reason). However, the public information I could see implied the system uses a RESTful API with JSON payloads and OAuth 2 flows.
The CLEAR database is the result of decades of Thomson Reuters shift from a "news and legal" company to a "surveillance" company. Its proprietary algorithms "stitch" records from disparate sources (e.g., a DMV record, a pizza delivery address, and a credit header) into a unique entity. When the call is made to CLEAR, a "360-degree view" of the individual is returned. This includes home and work addresses, utility bill history, social media, and "likely connections", including family and neighbors. We've lived with data brokers for quite some time. If it weren't for Thomson Reuters, I would suspect there are many others who would gladly bid for these multi-million-dollar contracts. What makes this different is the lack of any process or oversight. This system does not distinguish between "routine observation" and "targeted intimidation."
The uncomfortable truth playing out in the streets of Minneapolis, and increasingly elsewhere, is that oppression at scale does not require overtly malicious code. Simple interfaces, permissive access models, and the deliberate decision not to ask how the data will be used are ripe for abuse.
The "Apolitical" Trap
Too many software practitioners champion the belief that politics begins somewhere after the code is written (i.e., "That's above my pay grade."). It's a belief that asserts that value, power, and consequence are someone else's problem.
That belief is as convenient as it is false.
Political neutrality in software is a myth. Every system encodes assumptions about who may act, who may be acted upon, and what forms of behavior are made easy or difficult. Decisions about rate limiting, data retention, identity resolution, auditability, and access control are not neutral. They are governance mechanisms. They shape how power moves through a system.
When we build APIs that allow personal data to be stitched together across domains without meaningful review, when we expose enrichment endpoints without independently verifiable audit logs, when we treat "authorized user" as sufficient justification for unlimited access, we are not avoiding politics. We are making political choices - quietly, upstream, and at scale.
Claiming to be "apolitical" does not remove politics from your work. It simply defers those decisions to the actors most willing to exploit the capabilities you provide. That is not restraint. It is abdication.
If you build surveillance infrastructure and choose not to ask how it might be abused—because the conversation is uncomfortable, because it might threaten a contract, because "someone else would build it anyway" - you have not sidestepped politics. You have enabled it. You have encoded looking the other way into the system.
APIs do not just move data. They move authority. Pretending otherwise is not professionalism. It is how harm becomes routine.
The Stakes
There are many problems with the apps used for Operation Metro Surge. For example, giving poorly screened, previously convicted individuals the ability to stalk and harass will not end well. Encouraged to act with "absolute immunity", these agents are operating outside the rule of law - acting as judge, jury, and - in the tragic cases of Renee Good and Alex Pretti - executioner.
The media has (mostly) moved on, the replacement of Greg Bovino with "Border Czar" Tom Homan providing a convenient closure. But as I write this today, observers are still having their license plates scanned en masse, or boxed in and arrested for the crime of - checks notes - alerting neighbors to ICE activity. Are there likely to be mistakes? Certainly. But this isn't about policing or enforcement. When you're trying to terrorize a population into compliance and meet arbitrary quotas, the mistakes are a feature for pretext, not a bug.
Observers, in Minneapolis and elsewhere, will also have to adapt. If the government will not provide accountability for abuses of power and the ignoring of rights, then serving as a witness with a whistle and a camera is the best we can do. What that looks like without vehicles, to avoid the API dragnet, remains to be seen.
Wrapping Up
If you're outside of Minnesota and want to help, I strongly recommend Namomi Kritzer's collection of links. For technical practitioners, the https://iceout.tech/ website is worth a look. Finally, if you'd like a deeper dive into what drives the collective action and leaderless movement that has responded to Operation Metro Surge, I recommend this interview with organizer and activist Aru Shiney-Ajay.
Techdirt's Mike Masnick also has a great recap of the past month's events. Unbreaking.org has done a fantastic job detailing the alarming (and, frankly, gross) dissolution of data protections at the federal level. There will be so much to fix in better times.
Finally, have a conversation with your neighbors (that can be easier than you might think), look out for each other, and for God's sake, look at how your endpoints are being used.
Till the next edition,
Matthew (@matthew in the fediverse and matthewreinbold.com on the web)

* Because it will likely come up, a brief note about the pretext for Operation Metro Surge. The "immigration enforcement action" in the Twin Cities has been repeatedly, and misleadingly, linked to claims of "Somali fraud". The underlying embezzlement scheme was uncovered and prosecuted years ago, with its ringleader, who happens to be a white Christian woman, now serving a prison sentence. Minnesota citizens, on the whole, are staunchly anti-corruption. However, fraud investigations do not require armed patrols or mass street-level intimidation; they require accountants and subpoenas. As seen in other cities and communities, racialized accusations ("They're eating the cats and dogs!") are often deployed not to address crime, but to manufacture consent for actions aimed at intimidation, division, and social control.
Update: 2026-02-03 (Evening)
I hit publish, had an evening, put the kids to bed, and came back to find word of another kidnapping. This time, it was a cleaner, employed by a contractor, taken from a school for kids with special needs.